As attractive as it may seem conceptually, the Cyber Kill Chain® model can actually be detrimental to INFOSEC as it reinforces an old-school, perimeter-focused, malware-prevention thinking. No to say it is incorrect, rather that there are other perspective layers that should be worked in parallel.
Coined by Lockheed Martin, the term “Cyber Kill Chain®” has been widely used in the security industry to describe the different stages of cyber attacks.
However, whenever we look under the hood of the Cyber Kill Chain® diagram found at the Lockheed Martin website, we can’t help but try to scroll down farther than the diagram reaches. As it turns out, in a year that has observed successful targeted attacks on consumer-facing giants like Target, JPMorgan, and Home Depot — it has become clear that the actual scope of today’s cyber threats extends further than that of the Cyber Kill Chain®.
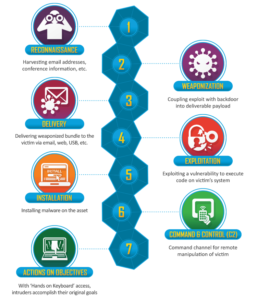
Developed by Lockheed Martin, the Cyber Kill Chain®
Beyond intrusion?
Lockheed Martin’s “Cyber Kill Chain®” model is intrusion-centric, which was the primary focus of cyber security when it was created, and continues to be focus of (too) much cyber security effort today.
The following is a brief description of its seven steps.
Step 1: Reconnaissance. The attacker gathers as much intelligence on the target as possible through any means available.
Step 2: Weaponization. The attacker uses an exploit and creates a malicious payload to send to the victim. This step happens at the attacker side, without contact with the victim.
Step 3: Delivery. The attacker sends the malicious payload to the victim by email or other means, which represents one of many intrusion methods the attacker can use.
Step 4: Exploitation. The actual execution of the exploit, which is, again, relevant only when the attacker uses an exploit.
Step 5: Installation. Installing malware on the infected computer is relevant only if the attacker used malware as part of the attack, and even when there is malware involved, the installation is a point in time within a much more elaborate attack process that takes months to operate.
Step 6: Command and control. The attacker creates a command and control channel in order to continue to operate his internal assets remotely. This step is relatively generic and relevant throughout the attack, not only when malware is installed.
Step 7: Action on objectives. The attacker performs the steps to achieve his actual goals inside the victim’s network. This is the elaborate active attack process that takes months, and thousands of small steps, in order to achieve.
In fact, steps 1 through 6 of the Chain relate solely to intrusion, which is, as we know from recent attacks, only a very small part of a targeted attack. Along these same lines, the Chain is disproportionate on an attack time scale: Steps 1 through 6 take relatively little time, whereas step 7 can take months.
Further, it’s worth considering that steps 1, 2, and 3 are not relevant from an operational point of view. These are just the documentation of steps an attacker may take behind the scenes, not something that security professionals can directly address or influence.
Then we have the fact that the Chain is completely malware-focused. But malware is only one threat vector facing today’s networks. What about the insider threat? Social engineering? Intrusion based on remote access, in which no malware or payload is involved? The list of threat vectors facing today’s networks is far, far longer than those covered by the Chain.
What we’re left with, after we eliminate non-practicable steps and steps that are too narrow in their focus to maintain broad relevance, is infinite space between steps 6 and 7 (“Command and control” and “Actions on objectives”). And it is in this vast place that today’s targeted attackers are thriving — many of them invisible to the Cyber Kill Chain paradigm or variant alike.
Layering your defensive approach
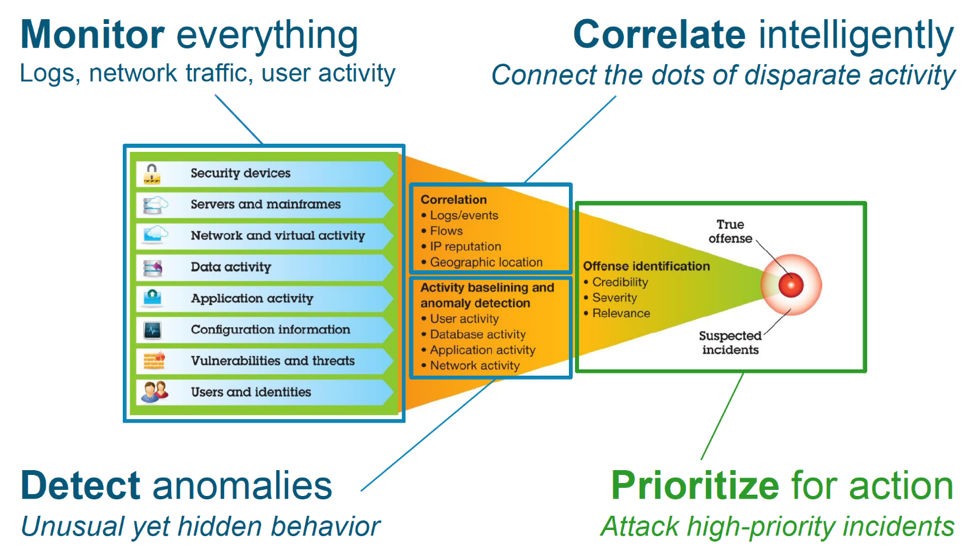
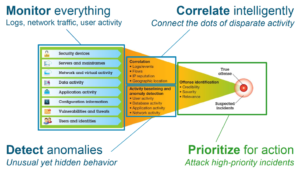
Cyber security risks can occur at a variety of levels and you need to set up security measures that provide multiple layers of defense against these risks. In general, when connecting to the Internet, you should not wonder if you will experience intrusion attempts or denial of service attacks. Rather, you should assume that you will experience a security problem. Consequently, your best defense is a thoughtful and proactive offense. Using a layered approach when you plan your Cyber security strategy ensures that an attacker who penetrates one layer of defense will be stopped or slowed by a subsequent layer.
Your cyber security strategy must include measures that provide protection and active SecOps defending across the following layers of the traditional network computing model. Generally, you need to plan your security from the most basic (system level security) through the most complex (transaction level security).
System level security
Your system security measures represent your last line of defense against an Internet-based security problem. Consequently, your first step in a total Internet security strategy must be to properly configure basic system security. There are FIM and rootkit monitoring defenses available at this layer.
Network level security
Network security measures control access to your network systems. When you connect your network to the Internet, you need to ensure that you have adequate network level security measures in place to protect your internal network resources from unauthorized access and intrusion. A firewall is the most common means for providing network security. Your Internet service provider (ISP) can provide an important element in your network security plan. Your network security scheme needs to outline what security measures your ISP provides, such as filtering rules for the ISP router connection and public Domain Name System (DNS) precautions. Sensors placed that monitor signal behavior and communications local and distant are imperative as confluent analysis data.
Application level security
Application level security measures control how users can interact with specific applications. In general, you should configure security settings for each application that you use. However, you should pay special attention to setting up security for those applications and services that you will use from or provide to the Internet. These applications and services are vulnerable to misuse by unauthorized users looking for a way to gain access to your network systems. The security measures that you decide to use need to include both server-side and client-side security exposures. Multi layered AV, Application control, rootkit monitoring, FIM, trace monitoring, process monitoring – reporting is immeasurable as a contributing layer of intel to active SecOps defense.
Transmission level security
Transmission level security measures protect data communications within and across networks. When you communicate across an untrusted network like the Internet, you cannot control how your traffic flows from source to destination. Your traffic and the data it carries flows through a number of different systems that you cannot control. Unless you set up security measures, such as configuring your applications to use the Secure Sockets Layer (SSL), your routed data is available for anyone to view and use. Transmission level security measures protect your data as it flows between the other security level boundaries or perimeters.
When developing your overall Internet security policy, you should develop a security strategy for each layer individually.
The takeaway:
- Over-focus on the Cyber Kill Chain can actually be detrimental to your network security posture.
Why? The Cyber Kill Chain model, as sexy as it is, reinforces old-school, perimeter-focused, malware-prevention thinking. And the fact is that intrusion prevention solutions cannot provide 100% protection. A persistent, highly determined, and highly skilled attacker will always find a way in. And once the attacker is past your perimeter, traditional Cyber Kill Chain-style prevention solutions like firewalls, sandboxes, and antivirus can’t help. Once they’ve bypassed these solutions, attackers are free to operate in your network unobstructed.
The answer? If you must use the Chain model, zero in on No. 7. Focus on detecting ongoing attacks — attackers that have already breached your perimeter — before the damage is done. Instead of analyzing old malware, deploy a breach detection system that automatically detects and analyzes the changes in user and computer behavior based on a layered approach that indicate a breach. These subtle changes are usually low-key and slow, and affect only a small number of computers, but the right analysis and context can flag them as malicious or suspicious and get you visibility as well as a gateway to automating your active SecOps defenses.
References:
Lockheed Martin
Retrieved from: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
Engel, G. (2014). Deconstructing the Cyber Kill Chain. Retrieved from: https://www.darkreading.com/attacks-breaches/deconstructing-the-cyber-kill-chain/a/d-id/1317542
Fielder, K. (2013). ISF congress post 9: Extending security intelligence with big data. Retrieved from: http://www.kevinfielder.co.uk/tag/security-intelligence/
IBM Retrieved from: https://www.ibm.com/support/knowledgecenter/en/ssw_ibm_i_73/rzaj4/rzaj40a0internetsecurity.htm
Fadili, A. (2016). The 8 layers of cyber security needed to protect your business. Retrieved from: https://info.focustsi.com/it-services-boston/the-8-layers-of-cybersecurity-needed-to-protect-your-business