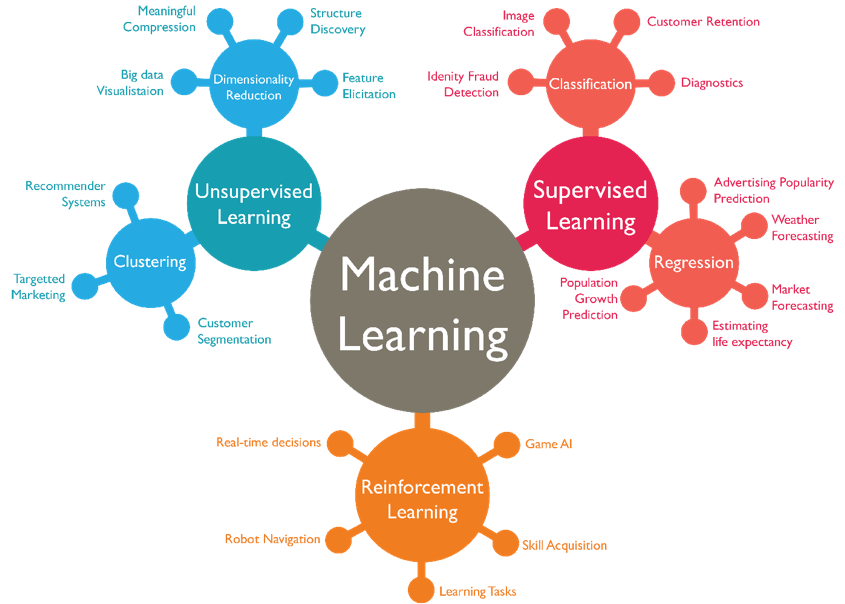
by Netorian | Sep 5, 2019 | Category #1
User Behavior Analytics + Network threat detection. The increasing focus on using security data analytics to extract insight and find or predict ‘bad’ has brought with it an influx of marketing promises of close-to-magical results. Among the offenders are those...
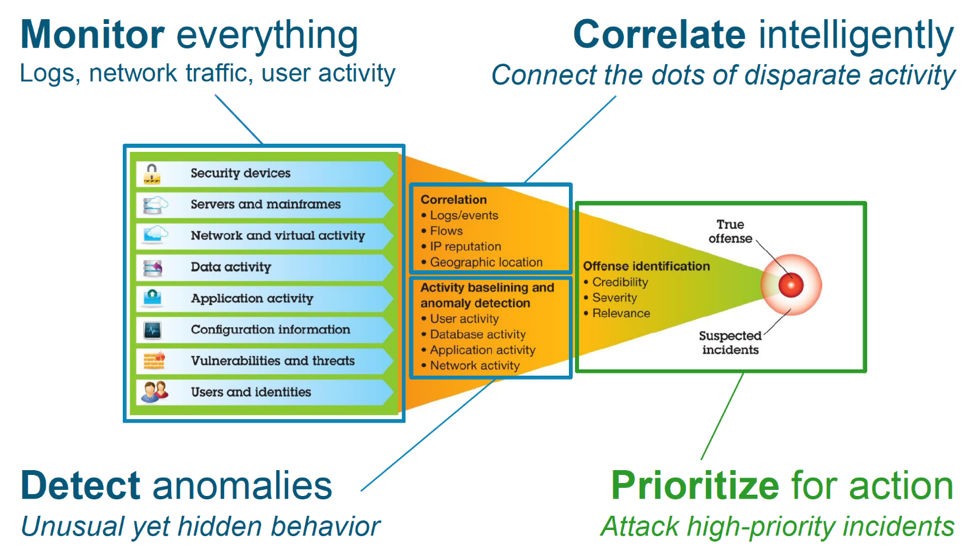
by Netorian | Sep 1, 2019 | Category #1
As attractive as it may seem conceptually, the Cyber Kill Chain® model can actually be detrimental to INFOSEC as it reinforces an old-school, perimeter-focused, malware-prevention thinking. No to say it is incorrect, rather that there are other perspective layers that...




